He is one of the most colorful figures in the hacker scene: IntelBroker repeatedly makes headlines with spectacular attacks on well-known companies. But who is this hacker? What motivates him? And what’s next for us?
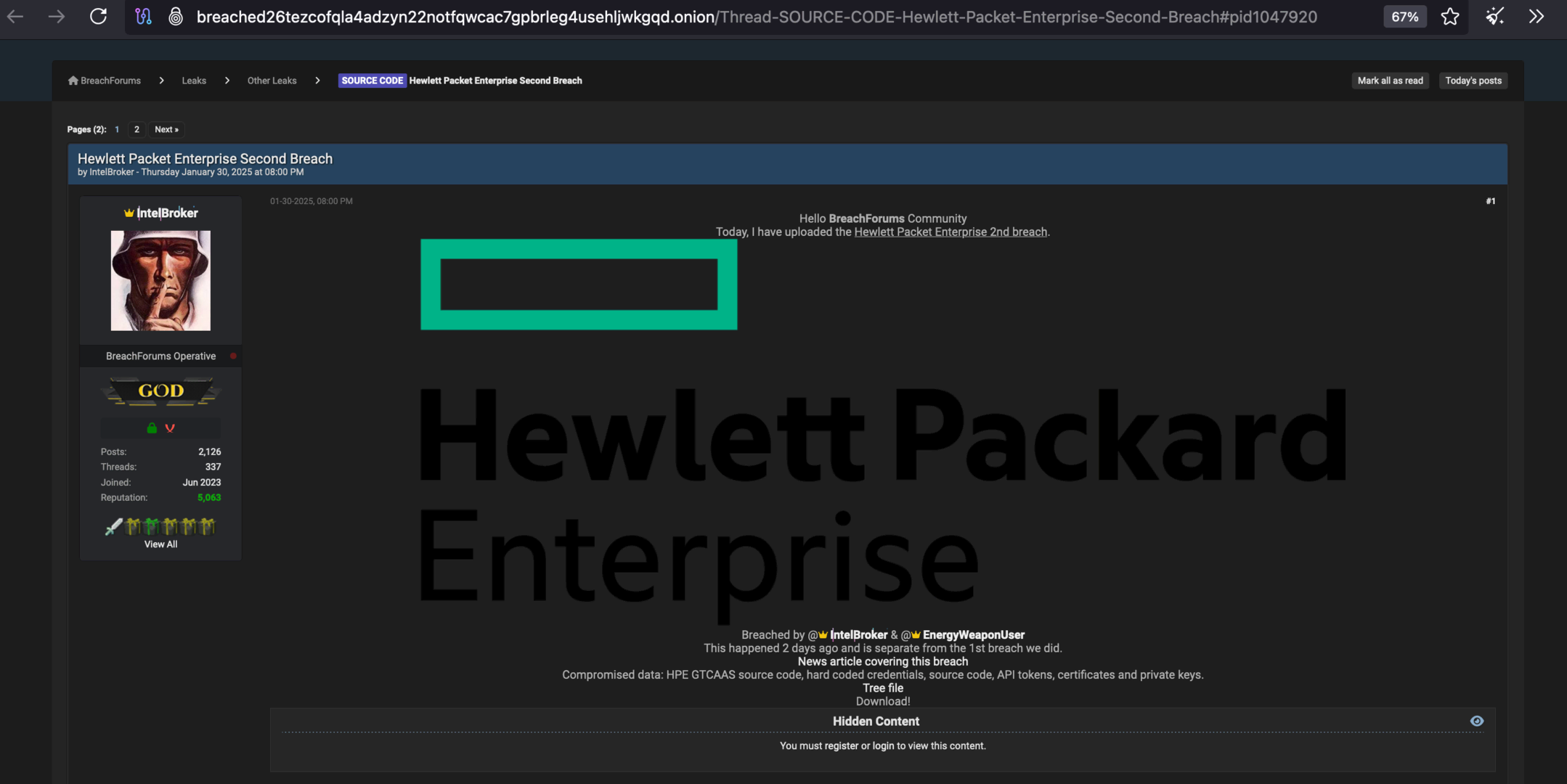
For Hewlett Packard Enterprises (HPE), one of the largest IT companies in the US with 60,000 employees, 2025 began with a serious security incident. IntelBroker claimed in a post on his notorious BreachForum that, together with two other hackers, he had obtained various company data and offered them for sale there. This was already his second theft from HPE. The stolen data this time included source code from private GitHub repositories, Docker builds, and certificates with private and public keys. Source code from Zerto and the server management interface iLO were apparently also included. As a “bonus,” there were accesses to APIs, WePay, and GitHub.
HPE responded immediately and announced that business operations were not affected. They also claimed no customer data had been compromised. Is that true? Unclear, because this sounds like a typical placation from almost all companies that have been attacked by IntelBroker in recent years. But perhaps everything wasn’t so bad, and one of the most prominent hackers has once again just staged a publicity stunt? Experience shows that IntelBroker’s claims should be taken quite seriously, even if there is the occasional industry-typical exaggeration.
For example, even Europol had to admit in May of last year that it had fallen victim to an attack. They also emphasized that core systems were not affected, but they had to acknowledge that the Europol Platform for Experts (EPE) was affected. This is a secure communication platform for collaboration between specialists from various police authorities. In addition, IntelBroker published some sample datasets and screenshots suggesting he had at least access as an authenticated user to the European Cybercrime Centre (EC3).
From Amateur to Professional Hacker
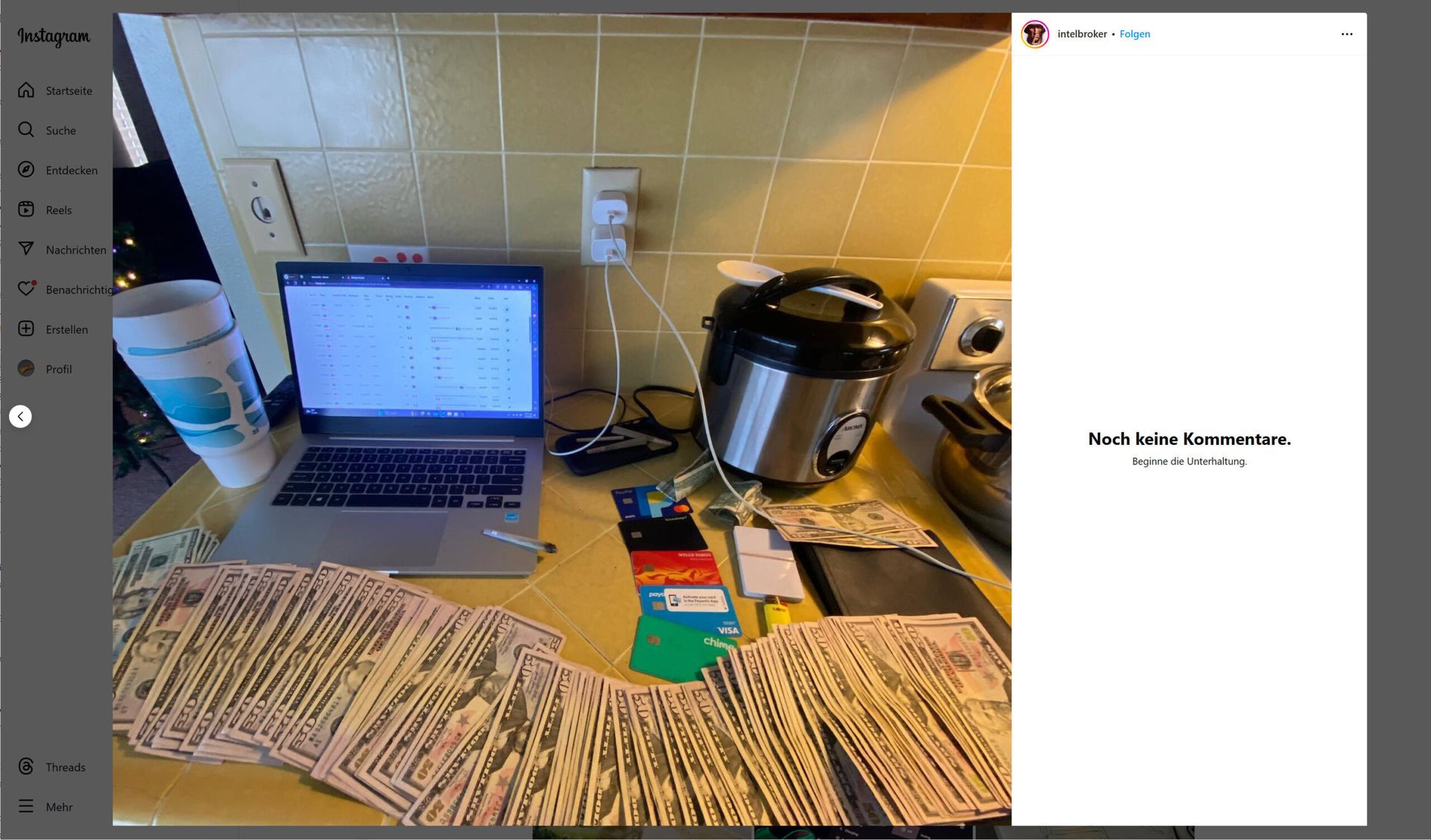
Even though one must realize that “IntelBroker” is a pseudonym behind which anything could be hiding, and that other people could also “adorn” themselves with it, there is a special fascination with this person. This is all the more true as IntelBroker not only draws attention through spectacular hacks but also knows how to stage himself skillfully. This starts with the takeover of BreachForum in August 2024 and even extends to an Instagram account with nearly 12,000 followers. On this account, whoever it is surrounds himself with the insignia of sudden wealth and uses as an avatar the image of a Wehrmacht soldier with a finger in front of his mouth. This is the new, now infamous, identifying mark of IntelBroker. The posts show iPhones, credit cards, cars, marijuana, and repeatedly large amounts of American dollar bills. Welcome to the gangster world.
How financially successful IntelBroker actually is can only be speculated about. In a remarkable interview in multiple respects on the German-language podcast “Inside Darknet,” he speaks of earnings of up to $800,000 per year. This interview is also remarkable insofar as it violates all journalistic standards. For example, it is not stated when and in what form the interview was conducted.
Moreover, it is translated by AI and output in German, allegedly because IntelBroker has poor command of English and to make the conversation appear “more fluid.” He gave another interview to the English-language security website “The Cyber Express,” which, however, published it only in heavily edited form and without any information about the background of the interview – in the form of excerpts. In both interviews, IntelBroker vehemently denies being part of a larger team. Because the hacker has repeatedly been associated with other groups, such as an Iranian Persistent Threat Group. In addition, IntelBroker belongs to a now inactive group of the BreachForum that bears the racist title “CyberNiggers.” But even in this context, IntelBroker repeatedly emphasizes his independence, even if the group members have apparently worked closely together, at least in part.
This brings us to the biography of the hacker, which, like all other statements, should be evaluated with caution. IntelBroker claims to be from Serbia but currently lives in Russia for security reasons. OSINT information shows a connection to a Minecraft account that is linked to him and that is listed as Serbian. Also, numerous VPN connections used by IntelBroker come from Serbia. All of this could just as well be a deliberately laid false trail. According to his own statements in the podcast interview, IntelBroker started hacking at the age of 20. And this, although he had previously worked only as a normal network technician in Serbia and had only simple programming skills. Through hacking online games and reverse engineering, he then gradually expanded his skills.
Apparently with success, because the list of companies he has attacked is as long as it is high-profile. Over 80 posts from him on BreachForum deal with leaks, access sales, and the sale of vulnerabilities. In addition, he mentions sales for access to over 400 companies. It can therefore be assumed that at least hundreds of companies have been targeted by him. Among the most prominent victims are, besides HPE and Europol, General Electric, AT&T, Verizon, Cisco, Apple, and AMD. Added to this are high-volume data leaks that can be traced back to him. In the Los Angeles International Airport Data Breach, for example, 2.5 million records with personal data were stolen. In the leak of the largest US Asian grocery store “Weee!”, eleven million customers were affected.
IntelBroker’s Modus Operandi
But how does IntelBroker proceed with his numerous attacks? All of his data breaches so far are opportunistic and untargeted, similar to ransomware attacks. IntelBroker mostly collects data from the first possible source and sells it to others. This distinguishes him from other hacker groups that aim for a complete compromise of the victim’s infrastructure and subsequently blackmail them. IntelBroker must therefore be clearly differentiated from the classic Advanced Persistent Threats (APT), although he would probably like to see himself as such a threat.
But IntelBroker has neither the resources nor the expertise to operate at this level. Moreover, he seems to have no clear objectives. Looking at groups like APT28 and Lazarus, these differences become clear. However, the term “group” is somewhat imprecise, and it would be better to speak of “clusters.” Attribution is difficult in most cases, and probably several teams often operate under a common umbrella. For example, the APT28 cluster pursues purely political and military objectives, while the Lazarus cluster pursues both political and financial goals.
IntelBroker’s data breaches are nevertheless by no means to be classified as a lesser threat. This is all the more true as he – once even unknowingly, as he himself admits – has already sold data to intelligence services. According to his statements in various forum posts, his modus operandi encompasses several techniques, such as exploiting vulnerabilities in publicly accessible applications to gain initial access to target organizations. However, it cannot be ruled out that IntelBroker also acquires information and data from other actors. Common methods for obtaining access data are also stealer protocols. From these, personal data for attacks can be obtained. From his leaks, it can also be inferred that IntelBroker executes unauthorized commands and manipulates accounts after intrusion.
Apparently, IntelBroker deliberately expands his privileges in compromised networks. This gives him access to higher levels and bypasses security measures. Like many other hackers, he applies obfuscation tactics to make his activities harder to detect. These activities could therefore go well beyond the initial access and persistence. In this respect, it is questionable whether the often quickly published statements of the affected organizations about the limitations of the damages are actually always accurate. After all, one should not underestimate that IntelBroker exfiltrates sensitive data through command and control channels, potentially gaining comprehensive sensitive information.
Who’s next?
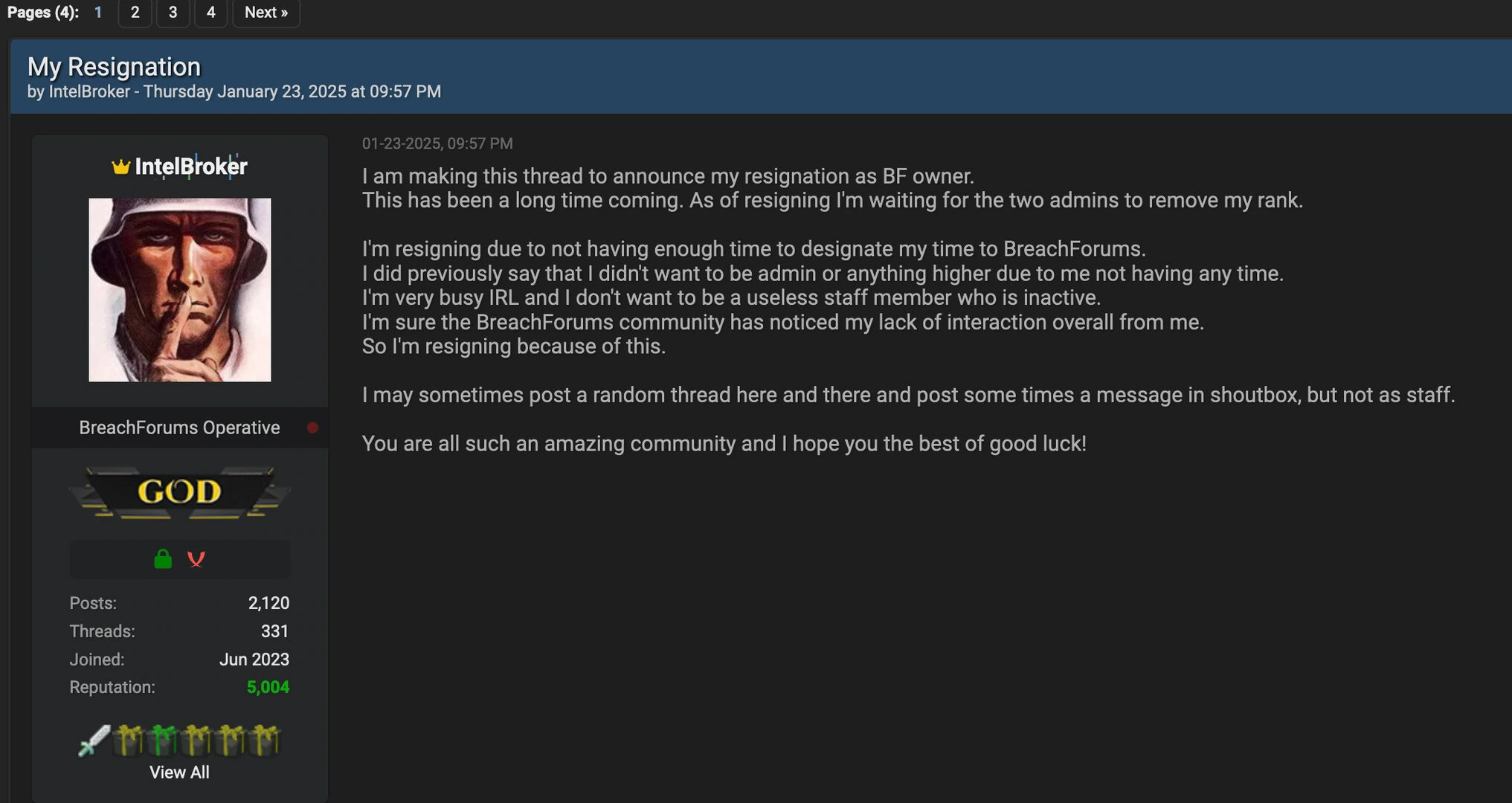
On January 23, 2025, IntelBroker surprised not only his community but also many observers of the hacker scene: In a post titled “My Resignation,” he announced that he was stepping down as owner of BreachForum. This does not mean that the forum is being dissolved, even though it was briefly taken offline by the FBI the year before. In this context, the then-owner (“Baphomet”) was arrested. He thus met the same fate as “Pompompurin” before him. That IntelBroker also fears arrest is rather unlikely. On the contrary, he writes that he simply no longer has enough time for BreachForum. He is currently very busy in his real life – whatever that may mean. For BreachForum, he already announces two new admins, and he himself also wants to occasionally speak up with a post. Just two weeks later, he followed his words with action. In February, IntelBroker already offered another breach, this time the database of the Peruvian pharmaceutical company Inkafarma.
So it’s not expected that IntelBroker will permanently retire. But even if he did, the danger to companies would not diminish. It is therefore important to continue to closely monitor the Dark Web. Because even if one will never find out the identity of IntelBroker and other hackers, one can at least analyze their approach – and derive appropriate measures to protect one’s organization.
In this context, securing and monitoring cloud environments is important first. But the clients must also be secured against infostealer breaches. An Endpoint Detection and Response (EDR) has established itself almost everywhere here. Beyond that, one should also monitor the Dark Web for breaches and immediately be alert when infostealer dumps become known. It is also important to check one’s own systems and applications accessible from the internet for vulnerabilities. It is advisable to establish vulnerability management here. After all, IntelBroker has often exploited gaps or misconfigurations in the past, for example in “Jenkins”.
So companies have a lot of work to do regarding their IT security. All these efforts will not stop attacks from hackers. But IntelBroker in particular has shown that threat actors often proceed opportunistically and choose the path of least resistance. And at least from that, one can protect oneself. In any case, every company can do without the “fame” of joining the long list as another victim of IntelBroker.
The information and analyses in this article come from the SECUINFRA Falcon Team, which specializes in Digital Forensics and Incident Response and conducts active research in the field of Threat Intelligence.