In the increasingly digitalized industrial landscape, the challenges in cybersecurity have grown considerably in recent years. The increase in targeted cyberattacks on operational technology (OT), i.e. control systems, devices and components in production facilities, is particularly worrying. OT and IT must work closely together to ensure effective cybersecurity.
Although both levels essentially pursue similar cybersecurity objectives, namely the protection and efficient operation of their respective systems, they differ significantly in several important aspects. One major difference lies in the systems and components used. While a high degree of heterogeneity prevails in OT environments and the systems used often remain in operation for many years, IT is characterized by greater homogeneity. The lifecycles of IT components are also significantly shorter. Network traffic also differs considerably. In OT environments, proprietary protocols are often used that are designed to meet real-time requirements. Minimal latency is crucial here to ensure the smooth operation of production systems. IT systems, on the other hand, use a large number of standardized protocols. Latency times are less critical here.
Another difference relates to vulnerability and patch management. In OT systems, patches are usually carefully planned and often applied outside of operating hours, as the systems are often in use around the clock and any downtime can lead to significant production losses. In contrast, regular patching in IT environments is standardized. Short downtimes, for example during an update, are generally less problematic. Finally, OT and IT differ in terms of protection goals and priorities. In OT systems, the focus is primarily on the availability of the systems, followed by the integrity and finally the confidentiality of the data. In the IT world, on the other hand, the confidentiality of data is the highest priority, followed by integrity and availability.
Multi-layered security concept
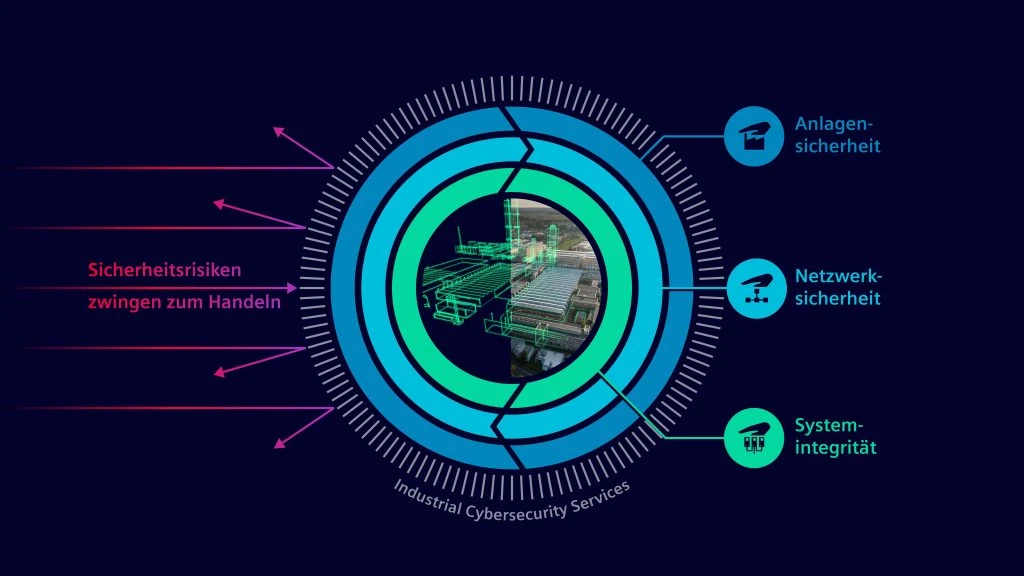
A successful attack on OT systems can not only cause production downtime, but also result in significant financial losses and long-term damage for companies. In addition, there are systems in OT environments that protect the safety of life and limb as well as the environment. In order to protect OT systems, special strategies and techniques are required that go beyond the usual IT security measures. A proven approach to securing OT systems is the so-called “defense-in-depth” concept, which is pursued by companies such as Siemens. This multi-layered security approach creates several levels of defense in the production environment and is based on the IEC 62443 series of international industry standards, which is considered the leading standard for industrial cybersecurity.
The Defense-in-Depth concept takes all key security factors into account, including physical access protection to systems, organizational and technical measures to protect production networks and control systems from unauthorized access, espionage and manipulation. This concept is supplemented by zero trust principles that focus on the verification and authorization of communicating units. In order to effectively improve OT security, plant operators should first carry out a comprehensive security assessment of their production environment. Such regular assessments help to identify potential vulnerabilities. Through these assessments, critical components and devices in plants that are particularly worthy of protection can be recognized and targeted measures can be taken to ensure their security. Various technologies and tools are used to implement the defense-in-depth concept based on the assessment results. In the area of network security, these include industrial firewalls that have been specially developed for use in production environments, as well as network segmentation systems that control data traffic between different areas of the production environment and minimize potential attack surfaces. In addition, intrusion detection systems (IDS) and intrusion prevention systems (IPS) are used to detect and block unauthorized access at an early stage.
As OT systems are often operated for many years without any major changes, available updates and patches must be implemented regularly. This is the only way to close known vulnerabilities. However, such measures must not interrupt production unplanned, which requires careful planning and coordination. In addition, the human factor is often a gateway for cyber attacks, which is why regular employee training should be carried out to raise awareness of security risks and to be able to implement the requirements of OT security in everyday working life.
Integrated teams of OT and IT staff
IT departments and production staff must work closely together to ensure secure production environments. One key to success is more interdisciplinary teams in which IT and OT specialists pool their respective expertise and learn from each other. While IT experts bring in-depth knowledge of network security, data management and system integration, OT personnel have a comprehensive understanding of the specific production processes, systems and their requirements. Only through this collaboration can a comprehensive security approach be developed. A joint security strategy is crucial in order to take the priorities of both areas into account. For example, patch management and access controls must meet both the security requirements of IT and the special operating conditions of OT. Such strategies help to reconcile the different priorities – availability in OT and confidentiality in IT. Integrated monitoring and response teams are crucial when it comes to quickly identifying and resolving security incidents. Such collaboration enables a rapid response to threats, as both IT and OT experts can take immediate action to minimize potential damage.
Future outlook and market trends
The future of OT security will be strongly influenced by developments in the field of artificial intelligence (AI) and cloud technologies. AI can not only be used to optimize production processes in new ways, but also to better detect and fend off cyber attacks. AI-supported systems can detect anomalies in the production process in real time and automatically initiate countermeasures. This increases the speed of response and minimizes potential damage. Another important trend is the increasing shift of security solutions to the cloud. This allows companies to monitor and manage their OT systems centrally – regardless of where the physical systems are located. This is particularly beneficial for globally active companies with distributed production sites.
The market for OT security solutions is growing steadily, driven by the increasing digitalization and networking of industrial systems. Technology companies such as Siemens play a central role in the development and implementation of security solutions that are specifically tailored to the requirements of industrial environments. Close cooperation with partners in the field of IT security makes it possible to offer comprehensive security solutions and services for industrial companies, including both locally installed and cloud-based systems.
| it-sa Expo&Congress Visit us in Hall 7 (Stand 423). |