With modern IT security technologies, companies can quickly implement Zero Trust solutions. Three examples show how they enable their employees to safely access cloud applications and company-owned applications from anywhere and surf the web without risk.
The threat level from cyber criminals remains high, forcing companies to take comprehensive IT security measures. They are dealing with complex environments characterized by remote working, BYOD and cloud platforms. Your employees access data from virtually anywhere and are often using private end devices that are not managed and secured by central IT.
In these modern environments, the zero-trust approach is increasingly establishing itself as the ideal way to achieve the highest security standard. It is replacing the classic security approach, in which users usually log in once with a user name and password and are then granted access to usually far-reaching resources such as entire networks or complete file repositories. In contrast, Zero Trust fundamentally distrusts everything and everyone and requires all data traffic to be checked and users, devices, applications and other units to authenticate themselves every time they access systems or data.
The implementation of an end-to-end zero-trust architecture is complex and time-consuming because it affects all areas of IT. However, particularly critical interactions can be secured comparatively quickly with the help of modern IT security technologies in line with the zero trust concept.
Secure remote access with BYOD devices
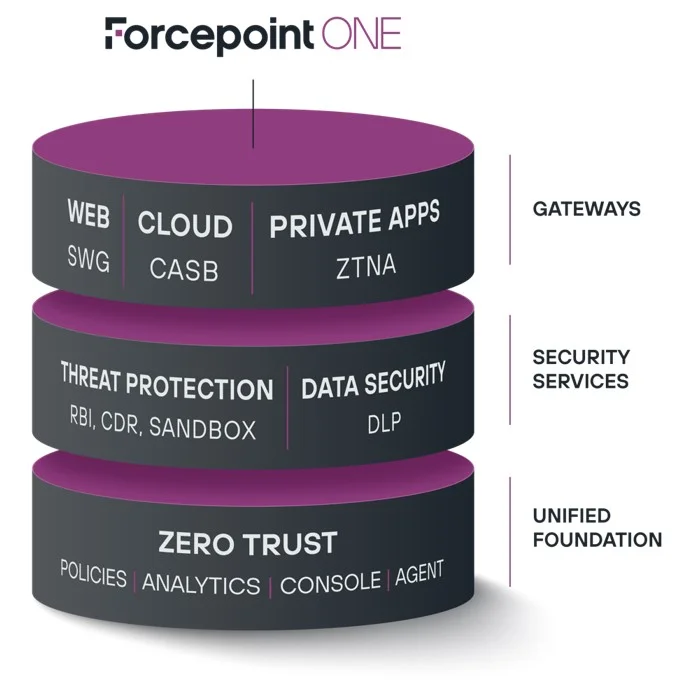
The first example of this is the protection of sensitive data in the public cloud when using BYOD devices. A Secure Web Gateway (SWG) in conjunction with a Cloud Access Security Broker (CASB) and Data Leakage Prevention (DLP) can prevent employees from downloading sensitive company information from a cloud platform such as Microsoft 365 onto a private end device. If it is a document that is not allowed to be saved on an unmanaged device according to company policy, the download is blocked and the employee is informed with a pop-up about why the download is not possible. The same mechanism also works in the other direction. If an employee wants to upload a sensitive document from Microsoft 365 to an insecure cloud service – such as a GenAI tool – this action is also prevented.
A second example is secure access with BYOD devices to company-owned applications that are operated either in a company’s data center or in a private cloud with an IT service provider. ZTNA (Zero Trust Network Access) technology can ensure that employees only have access to the applications they actually need for their work. SWG, CASB and DLP work together to ensure that employees cannot download any sensitive data to their private end devices. If employees want to upload documents to the company network or the private cloud, antivirus software scans the files for malware and blocks the upload if it finds any.
A third example concerns the safe use of the internet. URL filtering has always allowed companies to block websites that do not meet their compliance requirements and use antivirus software to prevent virus-infected files from being downloaded from the internet. In some cases, however, it may be necessary for employees to repeatedly access risky websites. For such cases, companies can implement Zero Trust Web Access with the help of Remote Browser Isolation (RBI) and Content Disarm and Reconstruction (CDR). These technologies ensure that only images of website content are streamed to employees’ browsers and that documents are completely disassembled before being downloaded and then reassembled without executable code. Employees do not notice any difference, but the websites and downloads are guaranteed to be free of malware.
Easiest with all-in-one systems
The easiest way for companies to implement such zero-trust solutions is with an all-in-one system that integrates all the necessary technologies. The security teams are then not forced to operate a completely separate policy management system for each separate isolated solution. This is not only extremely complicated and time-consuming, but can also lead to dangerous blind spots and additional attack vectors. All-in-one systems, on the other hand, allow security teams to manage security requirements holistically with a single set of policies in a central management console and enforce them across the entire IT landscape.
Modern systems also enable automated data classification. They have AI tools that reliably understand the content of documents and classify them accordingly. They also come with predefined guidelines for handling data worthy of protection and are able to adopt existing data classifications. Data classification, which in the past had to be carried out manually and was a real Sisyphean task, no longer causes any significant additional work for security teams and does not restrict their productivity.

















