A summary of the presentation by Dr. André Kudra, esatus AG, at the it-daily conference “Thought Leadership in IT 2023”. He explores the question of what distinguishes SSI from traditional IAM systems and what advantages SSI offers for exchange in the digital space.
1. Introduction to the topic and brief presentation of esatus AG
I would like to welcome you from Berlin and would like to give you a kind of “pioneering impulse”, because I am currently at the IT Security Law Day of the German IT Security Association, TeleTrusT, which can be described as a pioneer in IT security. My impulse deals with the topic of Decentralized Identity and represents a very important, fundamental architectural component that can be easily integrated into existing IT landscapes. As we have seen, the topic of AI also provides a certain amount of cause for concern and for action in the area of decentralized identity.
The term Self-Sovereign Identity – SSI for short – has already been mentioned in the introduction. Let’s take a look at what SSI now means and what the community has to say about it.
I would like to start by briefly talking about esatus AG, because we are often seen as an SSI or Decentralized Identity start-up. However, we have been on the market for three and a half decades – back then, digitalization was still referred to as IT! esatus deals with all topics relating to development operations, identity, security and especially decentralized identity. We are also very active internationally in various programs and community projects that many people around the world are working on.

Since 2015, esatus has been committed to the topic of Decentralized Identity, which we saw as an obvious solution. However, we have since realized that it is more of a marathon and that implementation is still in the starting blocks. There are currently still a few “waiting positions” due to EU legislation.
2. Artificial intelligence and deep fakes
As we heard this morning from one of the previous speakers from California, AI naturally offers us better solutions for some exciting topics. On the other side, the “dark side”, this of course also gives rise to very different threat vectors.
Some of you have probably already seen the video “This is not Morgan Freeman”, which shows very strikingly how you can put words into the mouth of a person – in this case a person of public interest – that they know nothing about. These are so-called “deep fake AI videos”. I also just received a video from a colleague that clearly shows how Chinese influencers are now optimizing their work by simply producing deep fake videos that they can use 24/7 to soundtrack their community, even though they may be lying on the beach…
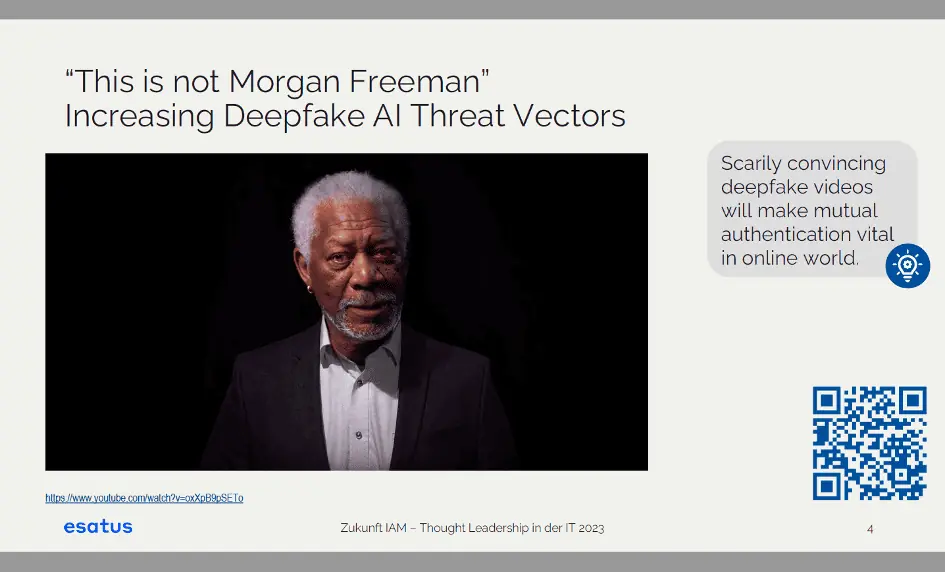
We therefore assume that we cannot build any kind of mutual trust in the online world if we do not carry out mutual authentication to know who I am actually talking to on the other side. This threat is very real, as these examples illustrate very well.
3. Architecture models and Zero Trust
There are of course great architectural models, and we have already heard a lot about them from the previous speaker, Ms. Roth.
In the area of authorization management and access control, there is the so-called zero-trust architecture model, which means that I must always assume that my systems are already compromised, that the attacker is already in my networks and that I have a problem. In other words, what we call traditional perimeter protection – a network secured by a firewall, etc. – is being completely called into question and converted to a zero-trust architecture model. The American government is now also very strongly demanding this.
It is essentially a NIST-defined architecture model, which you can see here on the slide.
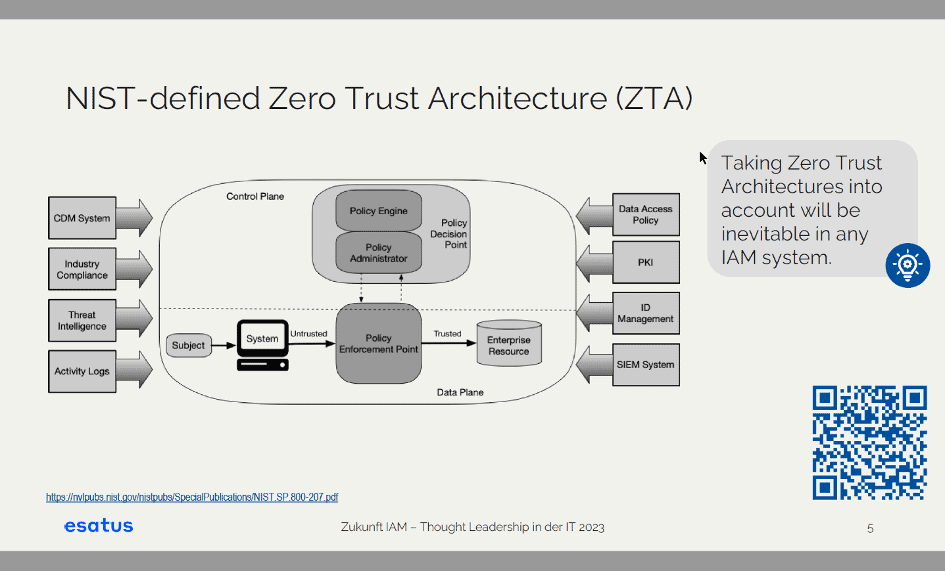
Zero Trust means that, in principle, every access to a system, whether machine to machine or by a person, must always be authenticated and that this authentication decision must always be made individually. This can be done by a policy engine, a policy enforcement plan or similar, which will not be discussed in detail here.
So the basic assumption is that we no longer have comprehensive perimeter protection, but that we have to authenticate every type of access in principle, at the time when it takes place and at the – let’s call it that – mini-perimeter of the application where it occurs.
The German Federal Office for Information Security (BSI) also very much welcomes this approach. However, Zero Trust is not standardized, it is very difficult to implement and maintain because you always have to define a policy that sets out the rules according to which you can access the system. This naturally requires a great deal of maintenance.
4. IAM and Decentralized Identity
Anyone who is familiar with Identity and Access Management (IAM) knows that an authorization concept has always had to be in place that defines “Who is actually allowed to do what in which system?” We heard the frightening words from California from a previous speaker: “If I dump all my secret content into the AI, how am I supposed to do access control?” An important impulse and an exciting challenge, because this is exactly the situation we have to deal with at the moment! It is therefore necessary for us to develop an authorization model or concept, which must then be transferred to a zero-trust architecture and maintained.
If we now ask ourselves how this can be made possible and what factors facilitate the implementation, the terms SelfSovereign Identity and Decentralized Identity come into play.
If you ask companies whether they already use Decentralized Identity, i.e. whether they work with verifiable credentials and digital wallets, the probability that the answer will be “yes” is extremely low. This is because it is a paradigm that first has to take hold, i.e. it first has to be perceived as a relevant factor in architecture models for companies and public organizations. Although our own company is using it for some customers and ourselves, it has not yet been rolled out across the board.
I would like to provide a little more background information here and illustrate the basic idea behind Decentralized Identity: ideally, you have an electronic wallet app on your smartphone, a digital wallet so to speak, in which your digital credentials are stored. The common international term for this is “verifiable credentials”. This can be an identity document, i.e. an ID card, a doctor’s certificate, a diploma, a certificate, an employee ID card, a bus ticket or a concert ticket. Everything that you usually have in paper form could be transferred to a credential and made available in your own wallet. This way, I have complete control over who can request such data and then receive it from me.
Via this wallet and the credentials, the end user regains a more powerful decision-making position with regard to their data.
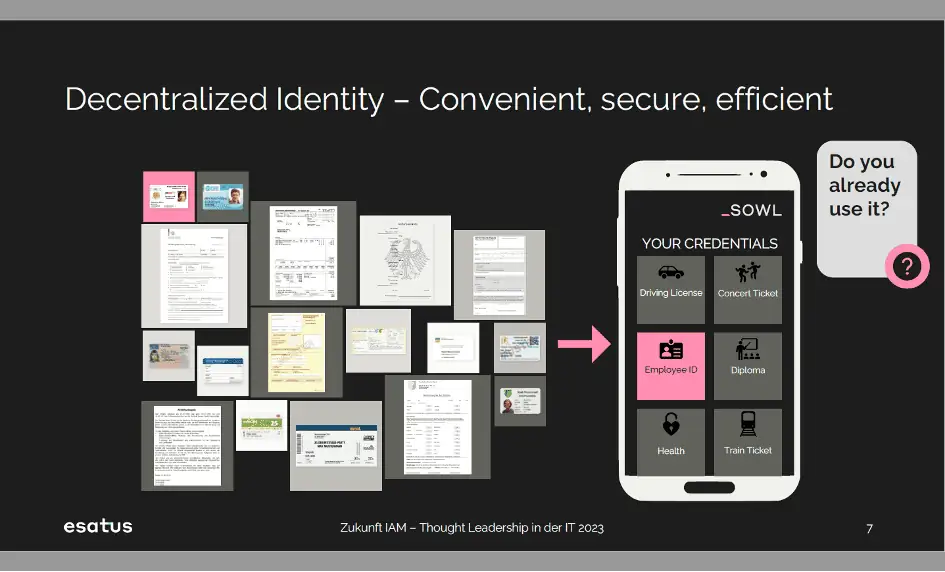
For example, if the company esatus wants to see your electronic identity document, it will send a request to your wallet. If you know esatus and can understand why the company needs the document, you will release it. However, if you walk past a coffee shop and they want all your credentials in exchange for a free cappuccino – then of course you won’t release them. Basically, the idea is that you can release your data to authorized interested parties in a self-determined way.
We call the whole topic Decentralized ID. It used to be called SSI (Self-sovereign Identity) because of the self-determined decisions I can make. The community was not so happy with this for various reasons and therefore prefers the term decentralized identity management.
The construction is therefore very simple: there is someone who can make the justified statement: You are an employee of esatus. The person sends you a corresponding credential to your wallet. You can then identify yourself to third parties as an esatus employee and they can verify that the credential was issued by esatus and has not been revoked in the meantime. This ensures a very high level of security.
This paradigm and the mechanisms behind it are identical regardless of the use case. Whether it’s healthcare, travel or banking – someone always makes a statement, packs it into a data package and this can then be reused elsewhere.
This is also underpinned by so-called Decentralized Identifiers (DIDs), which are pseudonymous characteristics, so to speak, with which these connections between the identities are established, which we will not go into at this point.
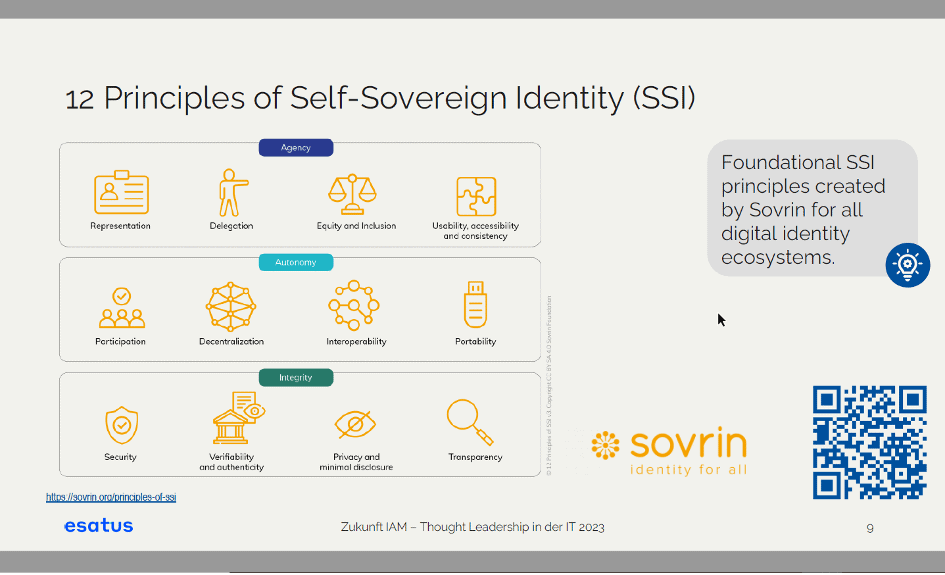
Sovrin was a pioneer in this area, building a network and presenting the principles of SSI very clearly, with a focus on the authorization of the end user by means of the decentralized ID. The user can make decisions and can also delegate rights to people they deem authorized (e.g. in the case of a child who is not yet legally competent or an elderly person who is no longer capable of acting). It is about maximum privacy and that the end user decides on their own data.