Aqua Security’s Team Nautilus presents a study detailing the infrastructure, tactics, techniques and modus operandi of the dangerous Kinsing malware. Kinsing first appeared in 2019 and targets cloud-native infrastructures, such as misconfigured APIs.
Aqua’s Team Nautilus discovered the malware in 2020 and has been monitoring Kinsing’s activities on the frontline ever since, identifying more than 75 compromised applications, including many popular cloud-native applications. The newly presented study entitled Kinsing Exposed: From Myth to Architecture – A Complete Cybersecurity Chronicle details the threats Kinsing poses to organizations worldwide. The report provides the cybersecurity community with detailed information about Kinsing, shows the extent of the threat and highlights the need for international cooperation in defense efforts.
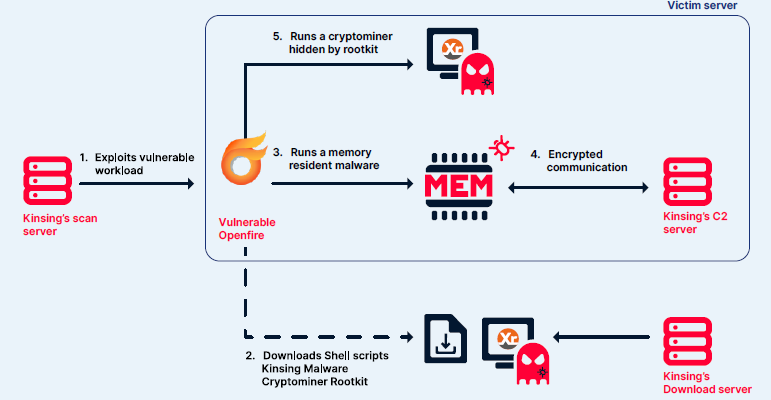
The three main components of the Kinsing malware: scan and exploit server, download server and command-and-control server.Image rights: Aqua Security
Dangerous malware that is constantly being developed further
Kinsing is constantly being actively developed and adapted by cyber criminals. Aqua Nautilus honeypots were attacked on average eight times per day by Kinsing, with numbers ranging from three to 50 attacks per day. Armed with anonymity, Kinsing exploits vulnerabilities or misconfigurations in applications, executes infection scripts, deploys cryptominers often hidden by rootkits, and maintains control of servers. Kinsing is also able to quickly integrate newly discovered vulnerabilities in popular native cloud applications into its botnet. The actors behind Kinsing tailor their ongoing campaign to maximize the effectiveness of individual attacks. The reach of the Kinsing malware extends around the world, with Shodan scans revealing potentially millions of daily attacks. The malware’s multi-layered approach proves that robust cybersecurity measures are needed to detect, mitigate and prevent the insidious attacks.
“The ongoing campaign by the cybercriminals behind Kinsing is constantly evolving to add new vulnerabilities and misconfigurations to the malware in cloud-native environments. The attackers often move faster than the defenders – which poses a real threat to organizations of all sizes,” emphasizes Assaf Morag, Director of Threat Intelligence at Aqua Nautilus. “Our report underscores the pervasive risk posed by Kinsing and urges the cybersecurity community to remain vigilant and united. The level of detail in our report demonstrates our team’s long-standing commitment to understanding and combating the Kinsing threat. Through years of continuous tracking and analysis, we are able to provide a comprehensive and more robust report that provides a full understanding of Kinsing’s modus operandi and better tools for defense.”
(pd/ Aqua Nautilus)
















