The winners of the it security Awards 2024 have been announced. They were awarded in the categories Management Security, Internet/Web Security, Cloud Security and IAM. The following manufacturers were honored: Abstract Security, Lasso Security, BxC-Consulting and Nokod Security.
Photo: The winners of the it security Awards 2024: Erez Shalom, Lasso Security; Richard Betts, abstract.security; Ulrich Parthier, IT Verlag; Marcel Fischer, BxC-Consulting; (from left to right); not in the picture: Dr. Ursula Ron, Nokod Security.
The it security Awards were presented on 22.10.2024 at the IT security trade fair it-sa in Nuremberg.
- abstract security won the Management Security category with its innovative security management solution that outperforms traditional SIEM systems. A key feature is the Abstract Security Engineer (ASE), an AI-powered technology that automates threat detection and enables real-time security analytics. By separating compliance data from security analytics, the platform optimizes data usage, reduces costs and speeds up threat detection. It also provides a one-click data storage solution that meets high data protection and scalability requirements. This enables companies to respond to threats more efficiently and quickly.
More info - Lasso Security received the it security Award in the Internet/Web Security category. Lasso Security was developed for companies that use Large Language Models (LLMs). The aim is to minimize the risks of uncontrolled use of LLMs, such as data poisoning and AI packet hallucinations, in which malicious data is smuggled into training models or non-existent malicious packets are generated. Another problem is prompt injection attacks, where malicious code enters systems via manipulated inputs. Lasso Security offers the first end-to-end solution specifically for LLMs to help organizations work safely and efficiently with these AI tools without compromising security.
More info - The CERIAL solution from BxC Consulting was the winner in the Identity & Access Management category. It automates the management of digital certificates in industrial environments and handles the entire lifecycle of certificates, from issuance to renewal. This reduces manual intervention and thus minimizes errors and downtime. Especially in the era of the Industrial Internet of Things (IIoT), where the number of networked devices is growing exponentially, CERIAL offers a scalable and efficient solution for managing certificates. It supports modern PKI protocols (such as EST), can be used across platforms and can be connected to various PKIs, which allows it to be flexibly integrated into segmented networks and reduces operating costs.
More info - Nokod Security is the name of the security platform that won an award in the Cloud Security category. It helps companies to manage security risks in the development of low-code/no-code(LCNC) applications and robotic process automation (RPA). What makes Nokod special is its ability to monitor all LCNC applications and automations in a central dashboard, automatically detect security gaps and vulnerabilities and offer immediate solutions. This includes protection against data leaks and injection attacks, which are often overlooked in traditional security approaches. The platform provides easy policy management and enables organizations to efficiently meet their security and compliance requirements while maximizing productivity through secure citizen development tools.
More info
“The year 2024 has shown that the innovation potential in the IT security industry remains extremely high.”
Ulrich Parthier, Publisher it security
The winners in detail:
Management Security
abstract security: Next generation security management
The topic is “Beyond SIEM”: The future of security operations platforms is called “abstract security” – a new star is visible in the security sky. Because the SIEM of the next generation will no longer be an SIEM. Why? Only 42% of successful attacks are detected by a traditional SIEM within a week of intrusion. This means their use is dubious in most cases. Why is this the case?
With conventional monolithic architectures based on index-based approaches, the alerting times are too long.
So new approaches are needed to solve the problem: Abstract security has developed a revolutionary platform with an AI-driven assistant to better centralize the management of security analytics.
The innovative solution goes beyond next-generation SIEM solutions by correlating data between data streams in real time. This allows compliance and security data to be used separately to increase detection efficiency and reduce costs.
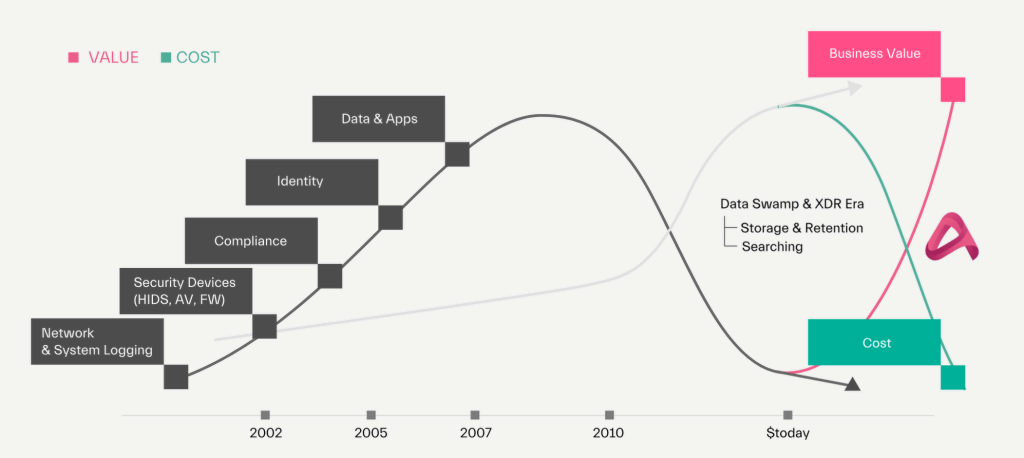
The difference
There is a fundamental difference between security analyses and compliance. Security analyses are streamed, compliance data is searched.
Abstract’s data management helps teams optimize data without compromising compliance or security effectiveness. This provides teams with immediate storage cost savings, faster discovery and powerful analytics capabilities.
For many vendors, the “future” of SIEM has become nothing more than another generation of logging search engines with a new dashboard and new features. But it’s time to stop modernizing the mistakes of the past, because 95% of the log data collected is useless for detection. A devastating figure. It’s time for a paradigm shift.
Users therefore need to separate their data for compliance and security purposes to save costs, increase efficiency and improve their detection capabilities.
In the past, too much focus was placed on data engineering, forcing security experts to learn the intricacies of ETL. This has resulted in Abstract, a no-code solution for data collection, management and transformation.
Internet/Web Security
Lasso Security: AI security solutions for LLM technology
Imagine a future where LLM (Large Language Model) technology is not only productive, but also secure. Lasso Security is working on exactly this future and equips LLM pioneers with innovative AI security solutions.
The uncontrolled use of LLMs is already creating new vulnerabilities for organizations of all sizes. Our goal is to help our customers and partners move forward confidently by giving them the tools they need to make progress without compromising security. Lasso is the first of its kind: an LLM-first end-to-end security solution for LLM pioneers.
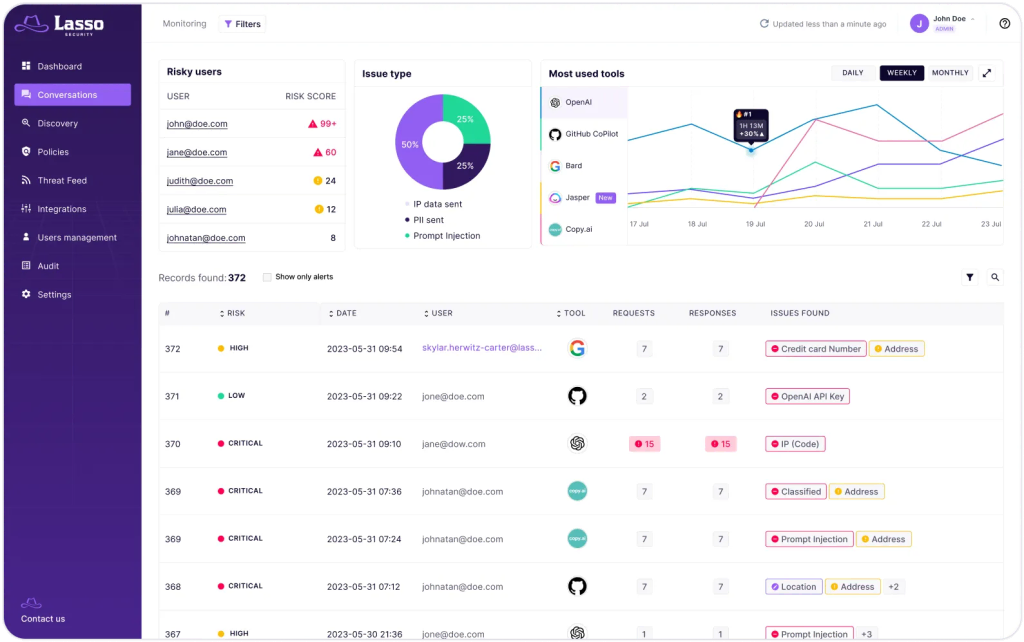
It is important to be aware that AI models are often trained with data that comes from uncleaned online sources. This means that the models can become an easy target for data poisoning attacks, where the attackers compromise the training dataset by injecting malicious samples into the AI model. AI packet hallucination is an attack technique in which GenAI tools are used to propagate non-existent malicious packets based on the model output provided to the end user. The integration of a hallucinated package into a production environment can pose a very serious security risk to the organization. Research by Lasso Security has shown that hallucinations are far from rare: 24.2% are caused by GPT4, 22.2% by GPT3.5, 64.5% by Gemini and more.
In addition, prompt injection attacks occur when an attacker inserts malicious code into a system via an input field or command. In the context of chatbots, this can happen via manipulated user input that manipulates the bot’s responses or accesses restricted areas. This type of attack can compromise data integrity, steal confidential information and disrupt chatbot services. Direct and indirect prompt injections are the two basic categories into which prompt injection attacks can generally be categorized. Both direct and indirect prompt injections pose significant threats to GenAI application systems.
Use case: Welcome to the coding highway
It seems like every developer is doing this these days. Well, almost. According to Gartner, 75% of enterprise software developers will be using these tools by 2028. With GenAI permeating almost every aspect of our personal and professional lives, it’s perhaps not surprising that generative AI tools based on Large Language Models (LLM) such as Copilot from GitHUb, Due AI from Google and CodeWhisperer from Amazon have become an integral part of the programming toolkit.
But there is one fact that should make security, risk management and compliance managers sit up and take notice: around 80% of them bypass security policies when using these tools, even though they know that GenAI programming wizards regularly create insecure code.
The main functions and benefits of the new Secure Code Assistant are productivity, efficiency, quality, consistency, speed and compliance with standards.
The risks
For all the benefits that GenAI code assistants offer developers, it is essential to ensure that the team is also aware of the associated risks.
These include:
- Predictable code security: AI models often generate code with predictable, static patterns that make it easier for attackers to exploit.
- Outdated libraries and frameworks: If outdated libraries and frameworks are integrated into the AI code wizard, unpatched vulnerabilities may be inadvertently introduced into the software, exposing it to unauthorized access.
- Data Poisoning: It is important to be aware that AI models are often trained with data that comes from uncleaned online sources. This means that the models can become an easy target for data poisoning attacks, where attackers compromise the training dataset by injecting malicious samples into the AI model.
- Disclosure of confidential information and code leaks: When using a Gen AI code wizard, the risk of confidential information and code leaks, i.e. unauthorized disclosure of source code, is all too real.
The threat of code leaks made headlines in April 2023 when it was reported that Samsung had issued an internal memo banning the use of ChatGPT and other chatbots. The decision was made after an unintentional leak of confidential internal source code and hardware specifications uploaded to ChatGPT by company engineers was discovered.
- Data protection during training: Sometimes a code wizard provides a live API key. This suggests that it may have been trained on codebases that contain real, confidential data. This raises concerns about privacy and security practices related to the training data for AI models.
- AI packet hallucinations: AI package hallucination is a type of attack technique that uses LLM tools to spread non-existent malicious packages based on model output provided to the end user. The integration of a hallucinated package into a production environment can pose a very serious security risk to the organization.
Based on research conducted by Lasso, it was found that hallucinations are anything but rare: 24.2% are caused by GPT4, 22.2% by GPT3.5, 64.5% by Gemini and more.
IAM
CERIAL: Fully automated management of digital certificates
In modern industry, digital certificates are an essential component for secure and efficient communication between networked devices. The CERIAL solution from BxC-Consulting, revolutionizes the management of these certificates by fully automating their issuance and renewal. The program was developed to relieve device operators of the time-consuming and error-prone manual management of certificates while ensuring the highest security standards.
It takes over the entire life cycle of the certificates – from issuance to renewal and management. Before a certificate expires, it automatically ensures timely renewal without the need for operator intervention. This ensures that your devices always have valid and up-to-date certificates, minimizing downtime and security risks.
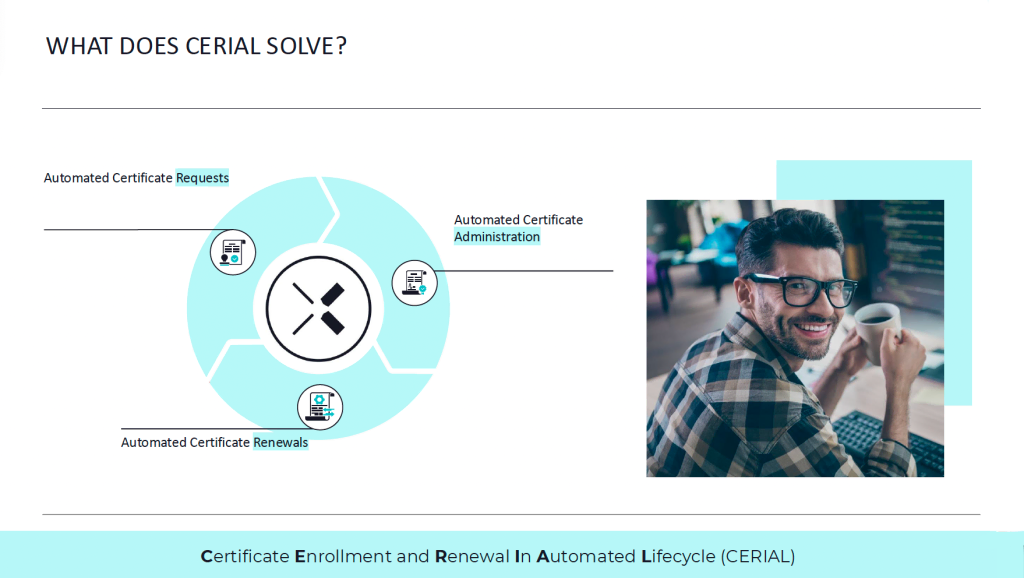
With the advent of the Industrial Internet of Things (IIoT), the number of networked devices in industrial environments is growing rapidly. Each of these devices requires a digital certificate in order to communicate securely and authentically. Manually managing this growing number of certificates is becoming increasingly impractical and inefficient. Companies are faced with the challenge of implementing scalable and automated solutions that enable them to maintain an overview and ensure the security of the entire infrastructure.
Innovation potential
- Use of modern PKI protocols (EST)
- Free use of the software without license costs, which greatly facilitates integration on the cost side
- Cross-platform support – Windows, Linux, Raspberry Pi
- Manufacturer-independent solution, connection of various PKIs possible
- No central management and control, so can be flexibly integrated into segmented networks
- Use on IIoT devices that are based on Linux
Cloud Security
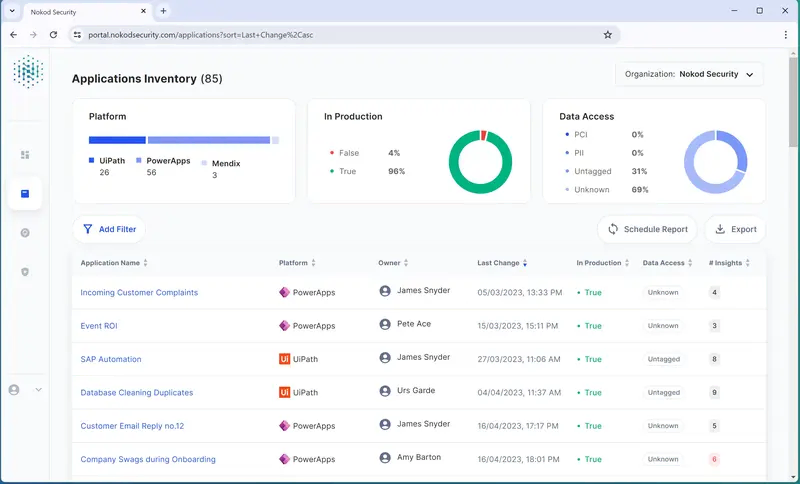
Nokod Security: Security for low-code/no-code(LCNC) applications
The problem: low-code/no-code (LCNC) app security
The solution: How can users integrate security into the lifecycle of their low-code/no-code application while keeping an eye on compliance risks and knowing what security measures to take? The answer is Nokod Security.
A traditional AppSec stack and its traditional AppSec processes do not protect the organization from low-code/no-code app threats, and attackers have all the knowledge and advantages.
Conclusion
Always one step ahead: with Nokod Security. So companies are able to:
- Manage low-code/no-code applications and RPA automations in one central location
- Manage cybersecurity and compliance risks of these applications
- Protection against data leaks, injection vulnerabilities, unpatched applications and components and more

















