Check Point encountered a curious malware case: The security researchers at Check Point Research (CPR) discovered that the developer of the new malware Styx Stealer made a serious mistake during debugging that leaked data from his computer.
In this way, CPR obtained a large amount of information, including the number of customers, profits, nicknames, phone numbers and email addresses, as well as similar data about the actor behind the Agent Tesla campaign. The Styx developer was in contact with one of the hackers behind Agent Tesla, Fucosreal, in a large-scale spam campaign.
The Styx Stealer is a derivative of the Phemedrone Stealer, which is infamous for exploiting the CVE-2023-36025 vulnerability in Microsoft Windows Defender SmartScreen. While Styx Stealer inherits the core functionality of Phemedrone, such as stealing stored passwords, cookies, browser AutoFill data, cryptocurrency wallet data and instant messaging sessions, Styx Stealer also includes advanced features: a persistence mechanism, a clipboard monitor and Crypto-Clipper, additional sandbox bypassing and anti-analysis techniques. With the crypto clipper functionality, Styx Stealer is able to steal cryptocurrency during a transaction by replacing the original wallet address stored in the clipboard with the attacker’s wallet address. The persistence mechanism ensures that the malware remains active on the victim’s system even after a reboot, allowing the crypto clipper to operate continuously and increasing the likelihood of a successful cryptocurrency theft.
While Phemedrone Stealer is open source and free, Styx Stealer is sold on a subscription basis. Subscriptions range from 75 US dollars (68 euros) per month to 350 US dollars (317 euros) for a lifetime license, with transactions being processed via the Telegram account (at)Styxencode.
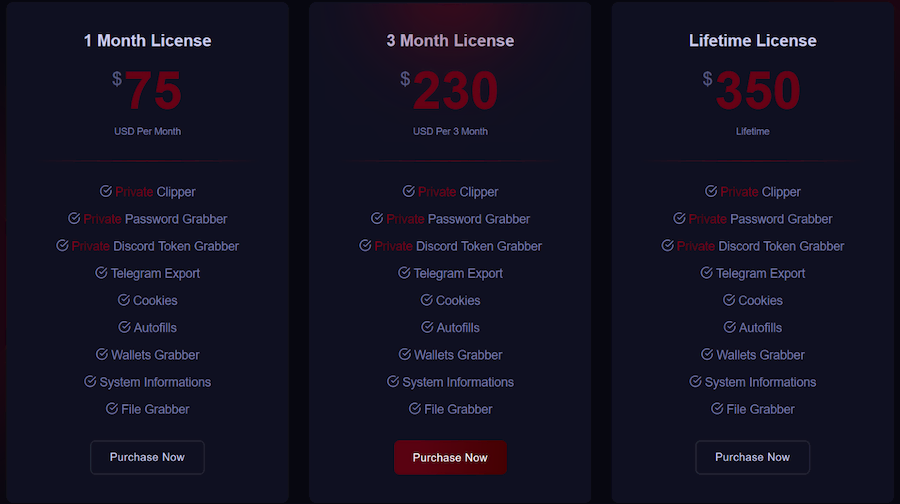
Image 1: Price list of the Styx Stealer on styxcrypter[.]com (Check Point Software Technologies Ltd.).
As mentioned above, CPR also discovered a link to Agent Tesla. The Agent Tesla malware is an advanced Remote Access Trojan (RAT) that specializes in stealing sensitive data from infected computers.
In March 2024, CPR discovered a spam campaign spreading the Agent Tesla malware and using the Telegram Bot API to steal data. Investigation of the Agent Tesla bot revealed that the attacker was primarily targeting representatives of Chinese companies, as indicated by the IP and email addresses that pointed to sources of Chinese origin.
CPR also identified affected companies in India, the United Arab Emirates and the Philippines. The victims come from various industries, including:
- Diamond industry
- Metal industry
- Glass production
- Environmentally friendly packaging
- Sea freight
- Wallpaper production
- Aluminum industry
Extraction of the Telegram bot token from the malware led to the Telegram bot created by the user Fucosreal. While monitoring this bot, an unusual document was intercepted that resembled the Phemedrone Stealer but was labeled as the Styx Stealer. This document contained a screenshot of the Visual Studio IDE with the PhemedroneStealer project, which contained a Telegram bot token and chat ID that matched Agent Tesla’s sample.
It turned out that the leak originated from the computer of the developer of Styx Stealer, also known as Sty1x. The data from the leak revealed two Telegram accounts (@styxencode, @cobrasupports) used by the developer, his email addresses, phone numbers, his approximate location in Turkey and his movements over a period of time. This also revealed Sty1x’s communications with customers and other cybercriminals, including Fucosreal.
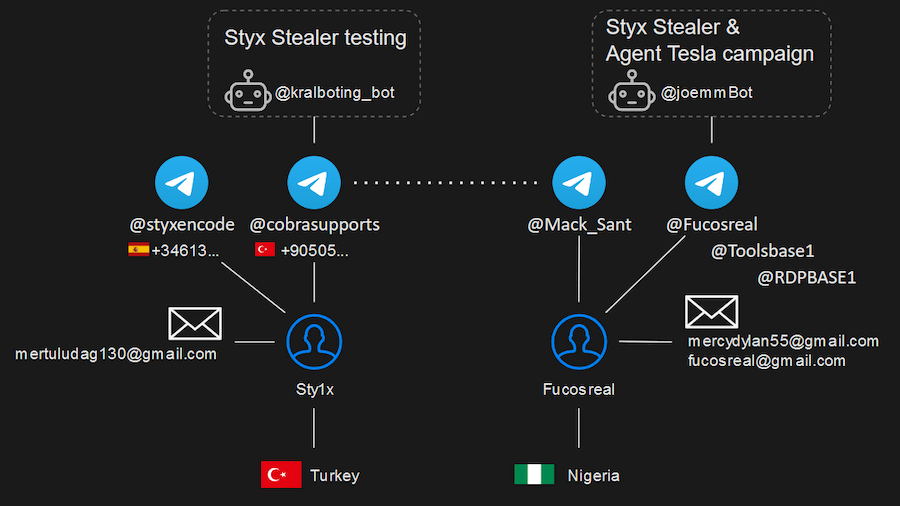
Figure 2: Accounts and pseudonyms of the Styx Stealer developer and the hacker behind Agent Tesla (Check Point Software Technologies Ltd.).
A total of 54 customers and 8 cryptocurrency wallets were identified, which presumably belonged to Sty1x and were used to receive payments. The total amount received within just two months of the start of the sale of Styx Stealer amounted to around 9500 US dollars (8596 euros).
Sty1x’s correspondence revealed that Fucosreal had provided the developer with a Telegram bot token for integration into Styx Stealer using another Telegram account, @Mack_Sant, to exfiltrate stolen data via Telegram.
Conclusion and recommendations
This campaign was characterized by the use of the Telegram Bot API for data exfiltration. The Telegram infrastructure was used instead of traditional command and control (C&C) servers, which are easier to detect and block. However, this method has one major drawback: each malware sample must contain a bot token for authentication. Decrypting the malware to extract this token gives access to all data sent via the bot and can reveal the recipient’s account.
The discovery of Styx Stealer and the findings about the developer’s vulnerability underline the importance of vigilance in the area of IT security. The case of Styx Stealer is a compelling example of how hackers can make mistakes due to basic security vulnerabilities. The creator of Styx Stealer lost important data such as Telegram accounts, emails and contacts. This critical OpSec flaw not only jeopardized his anonymity, but also provided valuable information about other cyber criminals, including the creator of the Agent Tesla campaign.
With such activities, it is extremely difficult to remain completely undetected. The constant surveillance of the hacker community means that the slightest mistake can lead to the exposure of not only the individuals involved, but also their associates. Even if these criminals are not arrested after being exposed, they know full well that their activities are being watched. If they continue their criminal activities, the evidence against them becomes even stronger. In the past, some criminals have stopped their activities after such reports.
To reduce the risk of being affected by such threats, the following is important:
- Operating systems and applications should be kept up to date with timely patches and other measures.
- Be careful with unexpected e-mails with links, especially from unknown senders.
- Awareness of cyber security should be raised among employees.
- If you have any doubts or uncertainties, we recommend consulting security experts.
(pd/Check Point)



